Encryption Security
The security of a cryptographic method is very important to the person relying on their message being kept secret. The security depends on two factors:
- The security of the method being used
- The security of the encryption key used
encryption security
The security of any encryption method should depend only on the encryption key being difficult to discover. It is not safe to rely on the encryption method (algorithm) being kept secret.
In the case of a shift cipher, the method is “a shift cipher is used.” The encryption key is the specific amount of shift used.
Suppose an army is using a shift cipher to send their messages, and one of their officers is captured by their enemy. It is likely the method and encryption key could become compromised. It is relatively hard to change encryption methods, but relatively easy to change encryption keys.
During World War II, the Germans’ Enigma encryption machines were captured, but having details on the encryption method only slightly helped the Allies, since the encryption keys were still unknown and hard to discover. Ultimately, the security of a message cannot rely on the method being kept secret; it needs to rely on the key being kept secret.
With that in mind, let’s analyze the security of the Caesar cipher.
brute force attack
A brute force attack is a method for breaking encryption by trying all possible encryption keys.
To make a brute force attack harder, we could make a more complex substitution cipher by using something other than a shift of the alphabet. By choosing a random mapping, we could get a more secure cipher, with the tradeoff that the encryption key is harder to describe; the key would now be the entire mapping, rather than just the shift amount.
Original: [latex]ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789[/latex]
Maps to: [latex]2BQF5WRTD8IJ6HLCOSUVK3A0X9YZN1G4ME7P[/latex]
While there were only [latex]25[/latex] possible shift cipher keys ([latex]35[/latex] if we had included numbers), there are about [latex]10^{40}[/latex] possible substitution ciphers. That’s much more than a trillion trillions. It would be essentially impossible, even with supercomputers, to try every possible combination. Having a huge number of possible encryption keys is one important part of key security.
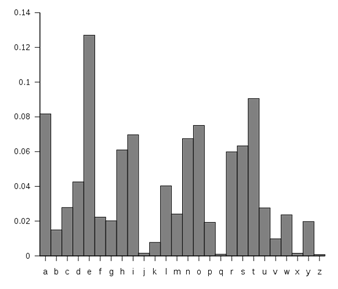
Unfortunately, this cipher is still not secure, because of a technique called frequency analysis, discovered by Arab mathematician Al-Kindi in the 9th century. English and other languages have certain letters that show up more often in writing than others. For example, the letter E shows up the most frequently in English. The chart to the right shows the typical distribution of characters.