- Compare ways of encrypting and decrypting data using shared symmetric-key methods
- Understand the basics of public key cryptography, including key pairs, digital signatures, and encryption/decryption
- Compare the pros and cons of using public key cryptography versus symmetric-key methods
Symmetric-Key Methods
The Main Idea
Cryptography involves using techniques to obscure a message so outsiders cannot read the message.
Encryption is the process of converting plain text or data into an encoded format that can only be read by authorized parties who possess the appropriate decryption key. The goal of encryption is to protect the confidentiality and integrity of the information being transmitted or stored.
Decryption, on the other hand, is the process of converting the encrypted data back into its original, readable form using the appropriate decryption key. Only authorized parties who possess the correct key are able to decrypt the information and access the original plain text or data.
The security of any encryption method should depend only on the encryption key being difficult to discover. It is not safe to rely on the encryption method (algorithm) being kept secret.
A brute force attack is a method for breaking encryption by trying all possible encryption keys.
A substitution cipher is a method of encryption that involves replacing each letter in a message with a different letter or symbol according to a predetermined pattern or rule.
You can view the transcript for “Private Key Encryption (Symmetric Key Encryption)” here (opens in new window).
Transposition Ciphers
The Main Idea
A transposition cipher is one in which the order of characters is changed to obscure the message.
Public Key Cryptography
The Main Idea
Public key cryptography is a method of securing digital communication by using two mathematically related keys: a public key and a private key. The public key is used for encrypting data, while the private key is used for decrypting it.
You can view the transcript for “Public Key Encryption (Asymmetric Key Encryption)” here (opens in new window).
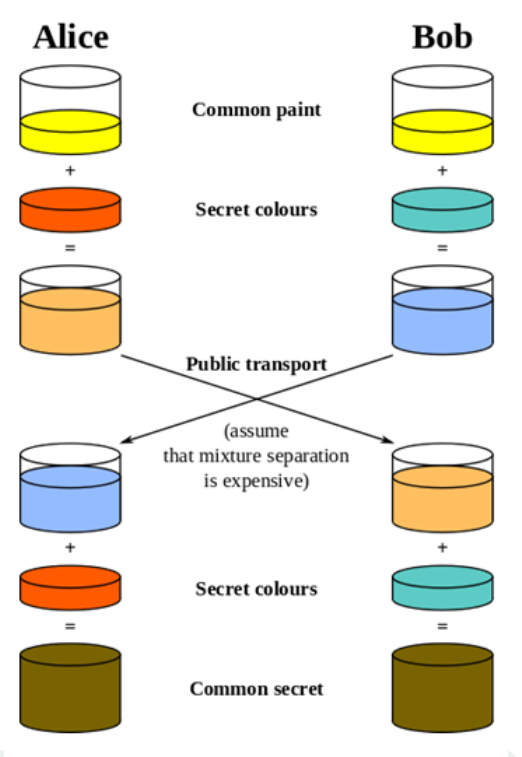
As an example, let’s consider mixing paint. It’s easy to mix paint to make a new color, but much harder to separate a mixed paint into the two original colors used.
Using this analogy, Alice and Bob publically agree on a common starter color. Each then mixes in some of their own secret color. They then exchange their mixed colors.
Since separating colors is hard, even if a snooper were to obtain these mixed colors, it would be hard to obtain the original secret colors.
Once they have exchanged their mixed colors, Alice and Bob both add their secret color to the mix they obtained from the other person. In doing so, both Alice and Bob now have the same common secret color, since it contains a mix of the original common color, Alice’s secret color, and Bob’s secret color.
They now have a common secret color they can use as their encryption key, even though neither Alice nor Bob knows the other’s secret color.
Likewise, there is no way for a snooper to obtain the common secret color without separating one of the mixed colors.
Pros VS Cons: Public Key Cryptography and Symmetric-Key Cryptography
Both methods have their own advantages and disadvantages, and it is essential to evaluate them before selecting the appropriate method.
Symmetric-key methods use the same key for encryption and decryption, and the key needs to be securely shared between the sender and the receiver. The encryption process is fast, and the data can be decrypted quickly. However, the main disadvantage of symmetric-key methods is that the key needs to be kept secret, and if it falls into the wrong hands, the data can be easily decrypted. Symmetric-key methods also suffer from a key distribution problem, where securely sharing the key between multiple parties can be challenging.
Public key cryptography, on the other hand, uses a pair of keys, a public key, and a private key. The public key is widely available and can be shared with anyone, while the private key is kept secret. Data encrypted with the public key can only be decrypted with the corresponding private key. Public key cryptography provides a secure solution to the key distribution problem since the public key can be widely shared without compromising the security of the encryption process. However, public key cryptography is computationally expensive, and the encryption process can be slow compared to symmetric-key methods.
The One-Way Function
You can view the transcript for “How does Modular Arithmetic work?” here (opens in new window).
- [latex]23 \bmod 7[/latex]
- [latex]15 \bmod 7[/latex]
- [latex]2034 \bmod 7[/latex]
The Key Exchange
You can view the transcript for “Diffie-hellman key exchange | Journey into cryptography | Computer Science | Khan Academy” here (opens in new window).