- Compare ways of encrypting and decrypting data using shared symmetric-key methods
- Understand the basics of public key cryptography, including key pairs, digital signatures, and encryption/decryption
- Compare the pros and cons of using public key cryptography versus symmetric-key methods
Symmetric-Key Methods
When people need to secretly store or communicate messages, they turn to cryptography. Cryptography involves using techniques to obscure a message so outsiders cannot read the message. It is typically split into two steps: encryption, in which the message is obscured, and decryption, in which the original message is recovered from the obscured form.
encryption and decryption
Encryption is the process of converting plain text or data into an encoded format that can only be read by authorized parties who possess the appropriate decryption key. The goal of encryption is to protect the confidentiality and integrity of the information being transmitted or stored.
Decryption, on the other hand, is the process of converting the encrypted data back into its original, readable form using the appropriate decryption key. Only authorized parties who possess the correct key are able to decrypt the information and access the original plain text or data.
One simple encryption method is called a substitution cipher.
substitution cipher
A substitution cipher is a method of encryption that involves replacing each letter in a message with a different letter or symbol according to a predetermined pattern or rule.
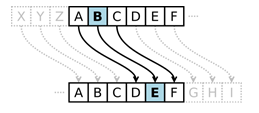
A simple example of a substitution cipher is called the Caesar cipher, sometimes called a shift cipher. In this approach, each letter is replaced with a different letter which falls in a fixed number of positions later in the alphabet. For example, if we use a shift of [latex]3[/latex], then the letter [latex]A[/latex] would be replaced with [latex]D[/latex], the letter [latex]3[/latex] positions later in the alphabet. The entire mapping would look like:
Original: [latex]ABCDEFGHIJKLMNOPQRSTUVWXYZ[/latex]
Maps to: [latex]DEFGHIJKLMNOPQRSTUVWXYZABC[/latex]
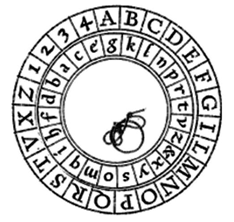
Notice that in the cipher above, the extra part of the alphabet wraps around to the beginning. Because of this, a handy version of the shift cipher is a cipher disc, such as the Alberti cipher disk shown here from the 1400s. In a cipher disc, the inner wheel could be turned to change the cipher shift. This same approach is used for “secret decoder rings.”